From January to August 2023, more than 360 million people were compromised by data breaches at corporations or institutions, according to a study conducted by MIT Professor Stuart Madnick and funded by Apple.
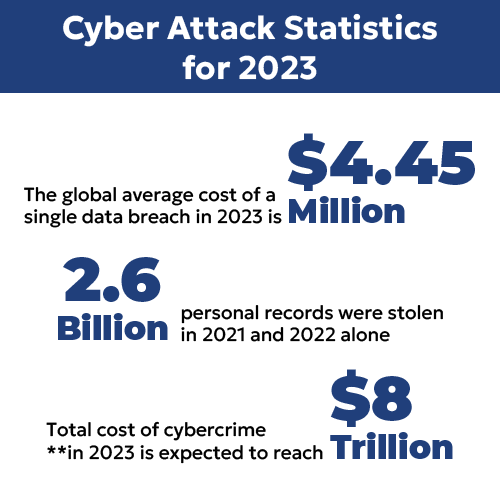
“We are at a record number of breaches and loss of data,” says Kirk Hasty, a Senior Technical Product Manager at Carbon Black. Just through September, 2023, data breaches were already 20% higher than in all of 2022.
With so much cybercrime in the news, it can be easy to lose track. In this article, we take a look month-by-month into some of the most significant attacks of the year to date.
A Key Event for Every Month
January: Royal Mail
It’s appropriate to open our profiles with an attack that was actually discovered the year prior, in November of 2022, when malware was first detected on the servers of the British postal service and courier company. In January of 2023, the LockBit Ransomware-as-a-Service caused printers at a Belfast distribution center to print their demands.
Mail service was disrupted for several days, and while the Royal Mail refused to pay the supposed $80 million ransom, the disruption and remediation may have cost the mail carrier $12.4 million.
February: City of Oakland
Early in February, 2023, the City of Oakland discovered that it had fallen prey to a ransomware attack by the Play group, which, although relatively new, has already attacked more than 30 organizations globally.
The attack forced a state of emergency, causing outages in city systems, and continued to plague residents for months, with sensitive private data leaked to the dark web for city employees including social security numbers, addresses, and medical data.
March: T-Mobile 2
“All the major communication networks deal with multiple attacks yearly, as the data and customer impact is huge,” says Hasty. This point was underscored in this year’s attacks on telecommunications giant T-Mobile.
As with the Royal Mail’s ransomware attack, the initial blow to T-Mobile actually began during the prior year and targeted an API, though it was not discovered until January of 2023. More breaches followed, in February and March, with 37 million customers in all having their data exposed.
This follows a prior attack on T-Mobile in 2022, where data for as many as 76 million customers was stolen, it’s ninth breach since 2018.
April: Western Digital
In April, another massive ransomware attack was revealed, this time at data storage company Western Digital. With more than 10 terabytes of customer data stolen in March, the hackers reportedly broke into the company’s internal database, giving them the ability to impersonate staff.
The stolen data was again partially leaked to the dark web, and also necessitated a two-week shutdown of their online store, and limited customer access to cloud data.
May: Storm-0558
For May, we profile the Chinese hacking group Storm-0558’s stunning invasion of Microsoft’s Azure cloud platform. Identified when a customer notified Microsoft of unusual access in June, this attack gave the hackers access to customer emails and potentially more at greater than 25 organizations, including some within the US government.
While the attack was disclosed in July, accounts were compromised as of May, and the groundwork laid far earlier—all the way back in April 2021—when a crashed workstation led to a dump of backup data that would become the source for the key needed for this break-in.
June: Reddit
The Reddit ransomware attack actually occurred in February, 2023, but the ransomware demand became public in June, with the BlackCat/ALPHV gang demanding $4.5 million for “the deletion of the data and our silence.”
The hack reportedly began as a phishing attack from a single account and amassed as much as 80GB of confidential data.
July: MOVEit
One of the biggest ransomware attacks of 2023 occurred via the file transfer software MOVEit, which was compromised by Russian group Cl0p. This attack exploited a zero-day vulnerability (unknown to the developers themselves), using SQL injection to give unauthenticated users access to the MOVEit database. From there they could gain information on or even alter the contents of target databases.
While the attack occurred and was patched in May, it was the cause of a record number of ransomware attacks by Cl0p in July.
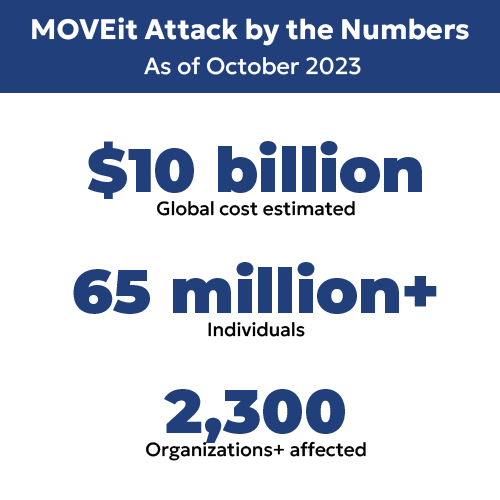
August: UK Electoral Commission
A disturbing breach of the United Kingdom’s national Electoral Commission was first disclosed in August, when emails and the personal data of as many as 40 million voters were accessed by unknown attackers for a substantial period. The breach first occurred in August of 2021 but was not discovered and removed until October of 2022.
A whistleblower told the BBC in September that the Commission had failed a cyber security audit in 2021 for running software on laptops and phones that was either no longer supported or not up-to-date with current security patches.
September: 2 Vegas Giants
Check out this PTP article for an examination of the attacks on Vegas entertainment powerhouses MGM and Caesars Entertainment during September. Both were hit by ransomware gangs, costing more than 100 million dollars in total damages.
October: 23andMe
Credential stuffing—wherein previously stolen user information such as passwords are tried on other sites—was the reported cause of a massive leak of highly sensitive data from genetics testing firm 23andMe in October, wherein as many as 6 million users may have had their genetic information accessed.
The attacker claimed to have millions of records and attempted to sell them online, targeting people by their genetic traits. This attack highlighted the personal responsibility we all have in keeping our accounts safe and should encourage all of us to take breaches of our data, however common, seriously.
November: ChatGPT
GenerativeAI superstar ChatGPT was briefly taken down in November, with responsibility claimed by Anonymous Sudan in what may have been a politically motivated attack.
In its first year of public life, ChatGPT has been subject to a few publicized cybersecurity events, such as in March, when a bug in the utility was exploited, leading to the release of personal user data before it was taken offline and successfully patched.
Check out this PTP article for a deeper look at potential security risks with emerging AI overall.
December: Norton Healthcare
With December not yet over, a sizeable breach in May came to light just last week involving the nonprofit Norton Healthcare. Another ransomware attack, it’s reported that the breach could impact 2.5 million patients.
This is just one of several successful attacks on US healthcare organizations in 2023, with an estimated 1 in every 4 Americans having their health data exposed in just the first three quarters of the year alone.
Conclusion
2023 was a record year for cybercrime, with the trend only expected to continue. While powerful innovations in AI can and will be leveraged by criminals, they must also be utilized proactively in the ongoing struggle.
“This calls for enhanced vigilance,” Kirk Hasty says, “advanced detection methods, and training for cyber defenders to use AI technology to enhance and improve their cybersecurity defenses.”
As discussed in this PTP piece, it’s essential for those in charge of securing these resources to always remain as vigilant as the attackers.
It’s also on all of us to guard against phishing attacks, still one of the most common and successful means of access for threats, to use good password habits, and to respond as soon as possible when we are all, inevitably, the victims of a data breach.





