It’s the end of July, 2024: do you know where your passwords are?
On July 4th a plaintext file containing nearly 10 billion passwords was released in the biggest dump of its kind. Gathered from varying sources, the file (named rockyou2024), updates prior releases, like rockyou2021 (with 8.4 billion passwords), and a 2009 data breach with tens of millions of entries, according to the Cybernews.
And while many entries are outdated, it still poses a significant risk, with the fallout likely to include additional data breaches, financial fraud, and identity theft.

Coupled with data compiled from other massive breaches (like MOAB), hackers use these files to attack systems by brute force, trying a flood of logins and passwords until they find combinations that work.
Credential stuffing attacks like these can trigger cascading problems for businesses and users alike (see Snowflake below), but the solution is fairly simple: never reuse passwords between logins.
In our cybersecurity roundup for June and July 2024, we look at the expanding Snowflake fallout, the Synnovis cyber attack, and Disney’s confusing Slack hack. We highlight spiking levels of Russian activity, and consider the startlingly high number of cybersecurity events triggered by insiders.
So don’t wait to change your passwords—although you should read this article first, as we digest NIST’s updated password creation and protection strategies for 2024!
The Snowflake Data Breach
A breach this consequential gets its own section, and cloud storage and services firm Snowflake has been the center of cybersecurity news this summer for the wrong reasons.
In what could eventually prove to be the largest breach ever, Ticketmaster (560 million records), Santander (30 million records), Advance Auto Parts (380 million), Lending Tree and QuoteWizard (190 million) are among the 165 clients that have already been impacted, according to Wired.
But the biggest hit may come to AT&T, with “nearly all” of their customers’ call and text records over six months stolen, per Ars Technica.
A report by cybersecurity firm Mandiant (a detailed analysis well worth the read) describes how these breaches began: with stolen customer logins leading to exfiltrated database dumps.
Mandiant determined that initial thefts likely came from infostealer malware, some via contractors also using systems for personal reasons, such as gaming and pirated software. These downloads likely included the malware that stole key information.
Their report, once again, points to the importance of utilizing multi-factor authentication (MFA), which, like the Change Healthcare ransomware attack, was not in place here:
“The affected customer instances did not require multi-factor authentication and in many cases, the credentials had not been rotated for as long as four years. Network allow lists were also not used to limit access to trusted locations.”
From Russia with Malice
Attacks on healthcare providers may be the cruelest form of cybercrime, subjecting innocent people to direct pain and suffering, and unfortunately 2024 has seen a steady stream of them.
The healthcare sector overall is one of the most regularly targeted, due to its large surface of interconnecting systems, and diagnostic services provider Synnovis was the latest victim to make the news.
Russian ransomware attackers Qilin dumped Synnovis data in June that included patient details and even specific test results. The attacks locked up systems, disabling English hospitals and medical services and causing numerous downstream problems, such as depleting national stocks of universal donor blood types, postponing thousands of appointments and outpatient procedures, and delaying life-saving kidney transplants for newborns and cancer treatments for those in need.
Russia, long a hotbed of cybercriminal activity, has seen its gangs flush with profits of late, with TRM Labs estimating that Russian hackers accounted for 69% of all crypto ransomware gains over the last year, at a staggering $500,000,000+ in proceeds for groups like LockBit, Black Basta, ALPHV/BlackCat, Cl0p, PLAY, and Akira.
Russian darknets also account for 95% of the global sales of illicit services and items.
In 2023, per BleepingComputer:
“-the three largest Russian dark web markets handled $1.4 billion in transactions, whereas the Western markets reached a total of $100 million over the same period.”
Also of note for June and July:
- In June, the US Commerce Department announced a rare ban on domestic sales from Russian cybersecurity and antivirus provider Kaspersky, who in July followed up by laying off its entire US staff.
- On July 1, Russian disinformation bots employing AI moved a fake news story from unvalidated websites, to trending topics across social media, and all the way to being the top search result on Google. All in 24 hours, according to reporting by Wired.
- The Russian hackers behind attacks on US water systems were uncovered, while cybersecurity company Dragos revealed how malware attacks on industrial control systems (ICS) in Ukraine successfully turned off the heat for 600 apartments over two days of freezing temperatures. They warn this same approach can be used against other infrastructure systems, in reporting by engadget.
- Russian hacktivists (or posing as hacktivists) broke into Disney’s internal Slack messaging and exfiltrated over 1 tebibyte of communications in July, in an incident that’s been blamed on varying causes (see insider threats, below).
Spotlight on Password Security 2024…
We opened with the rockyou2024 password leak, so it’s fortuitous timing that NIST also released their Digital Identity Guidelines in late July, providing updated password security best practices for 2024.
Their basics page includes the kind of best practices we love to discuss here at PTP, such as: require MFA, use strong passwords, use a password manager, always change defaults, install and update antivirus software, always update and patch, educate on phishing, and train all staff on basic cybersecurity.
The guidance also includes the following password management tips:
- Always use 12 characters and ideally more (and randomized), mixing upper and lower case, numbers, and symbols not in the dictionary. Never use any part of your name or a service’s name. And length, they say, is by far the most important of these tips for security.
- Use a password manager. This is becoming essential, as we should all never re-use passwords. These tools can also generate randomized passwords that cannot be guessed in relation to you.
- Never reuse a password and don’t use hints. A hint means a password can be figured out, which shouldn’t be possible. If your passwords are strong enough, hints shouldn’t be of any use.
- Contrary to conventional wisdom, changing your password too regularly can actually be dangerous, as it can introduce mistakes or lead you to choose something too easy. Let password manager tools create all new passwords, and as always, never use them in more than one spot. You are better off sticking with a good password for longer, than rotating through weak ones over and over again.
…and the Threat from Insiders
Closing out this edition of our bi-monthly look at the top cybersecurity threats and cyber defense strategies, is the surprising role so-called insiders play in cybercrime.
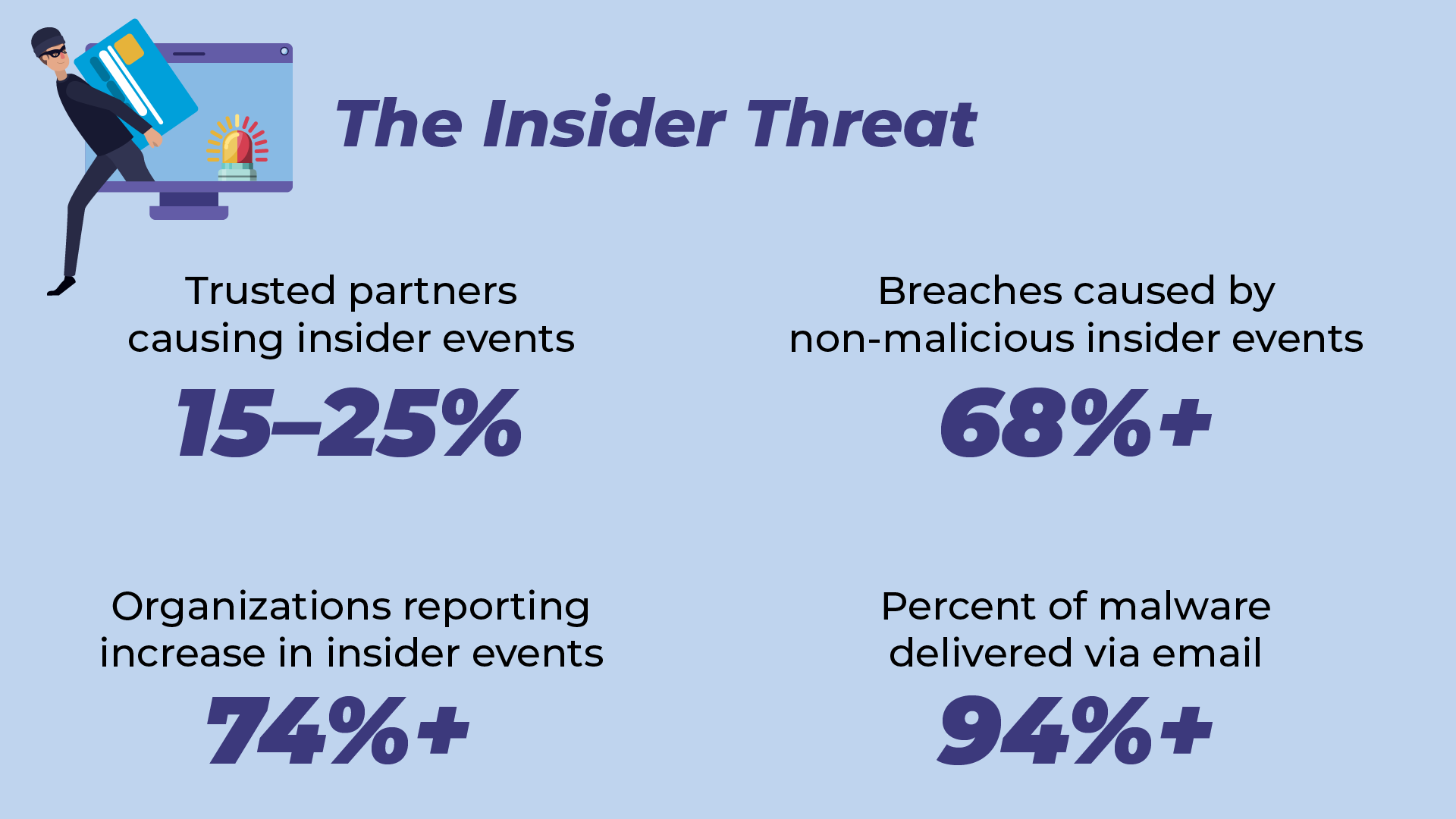
While cybercrime often conjures hackers at keyboards, cracking into systems with sophisticated techniques that penetrate a company’s defenses directly, the truth is that the majority of events occur because of insider actions.
Most aren’t malicious cyber attacks from insiders (though these do occur, as in this stunning case of a North Korean operative getting hired at a US security vendor under a false identity and immediately commencing to hack them), but are instead accidental.
This can be something as simple as accidentally sending emails to the wrong address, or by clicking a link in an email. And in theory, it should be one of the simplest of our defenses to shore up.
Phishing becomes increasingly sophisticated all the time, from fake live chat agents (impersonating known support for malicious purposes) to callers pretending to be from your own company’s IT department.
The Disney Slack hack has been blamed on various things, with the hackers initially claiming an internal employee (who they named) intentionally leaked the data.
But recent reporting (by PC Gamer) suggests another form of insider threat may be to blame: a mod (containing infostealing malware) for a popular game downloaded and played on the same machine where the Slack channel was in use.
In this case, an insider event may have opened the door for the theft of over a tebibyte of internal Disney data, due to a mistake very similar to the ones proposed by Mandiant for the Snowflake breach.
Conclusion
That concludes our coverage of the top cyber attacks and news from June and July 2024. Subscribe to The PTP Report or check it out on our website for continued coverage of all the latest cybersecurity threats.
[And for help with your own cybersecurity needs, contact PTP for onsite or remote consultants.]
You can also catch up on our prior bi-monthly roundups here:
References
RockYou2024: 10 billion passwords leaked in the largest compilation of all time, Cybernews
The Snowflake Attack May Be Turning Into One of the Largest Data Breaches Ever, Wired
Nearly all AT&T subscribers’ call records stolen in Snowflake cloud hack, Ars Technica
Toll of Snowflake Hack Widens With Theft of AT&T Text, Calling Data, Bloomberg
UK’s NHS says hackers have published data stolen in ransomware attack, Reuters
NHS cyber attack delayed my baby son’s life-saving kidney transplant, The i
Breast cancer patient reveals how Russian hackers forced her to delay surgery, The Telegraph
Russian ransomware gangs account for 69% of all ransom proceeds, BleepingComputer
Kaspersky to shut down US operations, lay off employees after US government ban, TechCrunch
How Disinformation From a Russian AI Spam Farm Ended up on Top of Google Search Results, Wired
Russia-linked hackers cut heat to 600 Ukrainian apartment buildings in the dead of winter, researchers say, Engadget
7 password rules to live by in 2024, according to security experts, ZDNet
Disney investigating massive leak of internal messages, BBC
A furry hacktivist group has breached Disney, leaked 1.1TiB of data, and says it’s because Club Penguin shut down, PC Gamer





