There’s a famous scene in the film Enter the Dragon (1973) where Bruce Lee’s character chases an enemy into a room of mirrors but cannot fight him: he is increasingly frustrated and unable to identify the real foe from the decoys.
Now imagine this tactic applied to cybersecurity: where perfect replicas of systems are presented as targets, fooling cybercriminals into attacking virtual models.
This so-called honeypot—traps designed to draw attackers away from the real thing—is increasingly becoming a reality. And while a hall of mirrors won’t necessarily allow organizations to eliminate cybercrime, it can give an otherwise impossible level of insight: learning what the attackers are after, how they operate, and what weaknesses they’ve exploited to get in.
And even more importantly, these ghost versions can register the attack and protect the real thing, warning the security team to the threat at hand.
This is just one of a number of cybersecurity benefits that are increasingly becoming a reality with the rapid integration of digital twins into cybersecurity.
Sadly it’s not all magical armor for companies: a digital twin may also expose an additional attack surface to criminals, and in today’s edition of The PTP Report, we consider both: how digital twins are exploding, ways they must be accounted for by security teams, and the benefits they provide both now and into the future for cyber defense strategies.
The State of Digital Twins
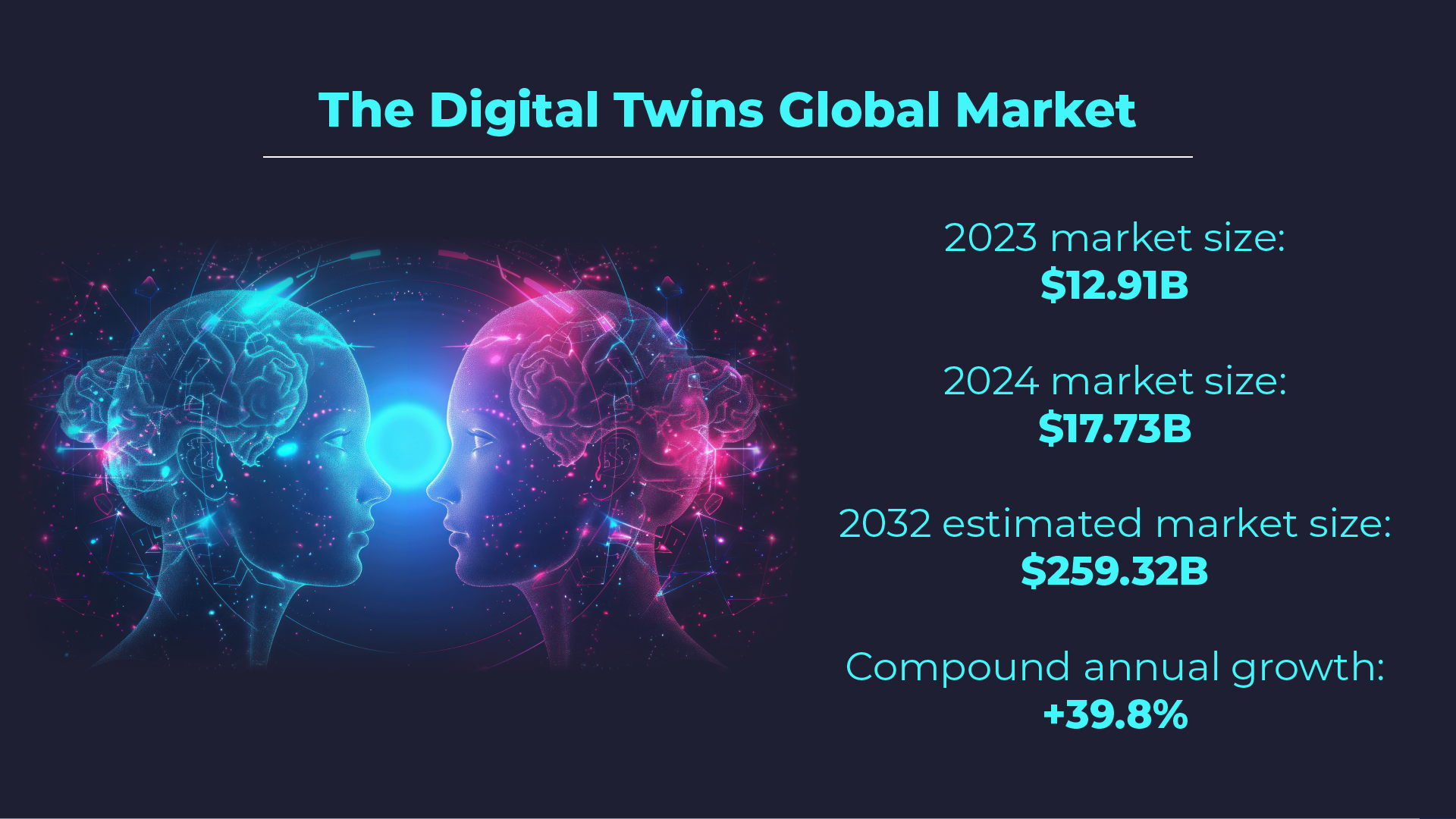
A digital twin is more than just a virtual copy of a real thing, it’s high-fidelity, augmented by real-time data (often with a two-way flow between the model and the real). And it evolves over time, like the real thing.
Digital twins have all manner of uses, and likely originated in the current form with NASA’s work to simulate, monitor, and test spacecraft and their systems decades ago. Originally associated only with expensive, high-risk systems of scale, emerging technologies (IoT, AI, Big Data) have made them increasingly practical, and affordable, across a wide spectrum of uses.
[For more on digital twins in Industry 4.0, see prior editions of The PTP Report.]
AI-powered digital twins are expanding far beyond manufacturing. Utilized in smart cities, airports, and seaports, they monitor and manage infrastructure in real-time, working to optimize classic bottlenecks like traffic flow and boost energy efficiency.
In healthcare, digital twins help doctors predict outcomes and personalize patient treatment, and in marketing they’re used as synthetic users. Avatars, or digital twins of specific individuals, have been in use for years in both entertainment and journalism, and as influencers, with some racking up millions of followers.
At PTP, we’re currently putting them to use to resolve challenges in recruitment, in partnership with MindBank.
More to Attack
But like the explosion of virtually any new technology, the digital twin also brings security challenges. With access to real-time data, modeling and often enabling controls of the real thing, these virtual copies can expose access that may have previously only been available on-site.
It is further complicated by the fact that cybersecurity teams may not even be fully aware of their usage, let alone in control of their access.
Alfonso Velosa, research VP of IoT at Gartner, tells CSO’s Alex Korolov that new smart assets—like freezers, trucks, backhoes, or elevators—often include a digital twin out of the box, and this can be difficult to manage if teams are not in control and prepared to manage them.
“Most of the operational teams will need a streamlined and cross-IT—not just CISO—set of support to integrate them into their broader business processes and to manage security.”
The communication between these twins and their source can be attacked, making the security of digital twins often as critical as the real thing. IoT devices are also often not designed with security in mind, and their integration can widen this attack surface even further.
Cybersec Applications
While digital twins may initially offer more opportunity for criminals than security teams, they are increasingly being employed in meaningful ways for cybersecurity, with the National Institute of Standards and Technology (NIST) actively researching this application in the near term.
One example from the University of Michigan and NIST built a cybersecurity framework of AI and digital twins, using off-the-shelf 3D printers. Launching a series of aberrations at the printers, some routine (such as modifying the temperate of the space the printers run in), and some calculated cyberattacks, they used this digital twin framework for an effective means of real-time monitoring.
The digital twins detected anomalies and passed them to additional models to determine the cause, checking against known libraries. Dangers that weren’t recognized were flagged and called for a human expert’s immediate attention. These cases were then either addressed as cyberattacks or added to the library or legitimate deviations.
Digital twins of complex computing systems with their hardware spaces, such as network topologies, are currently being used in cybersecurity, giving benefits such as:
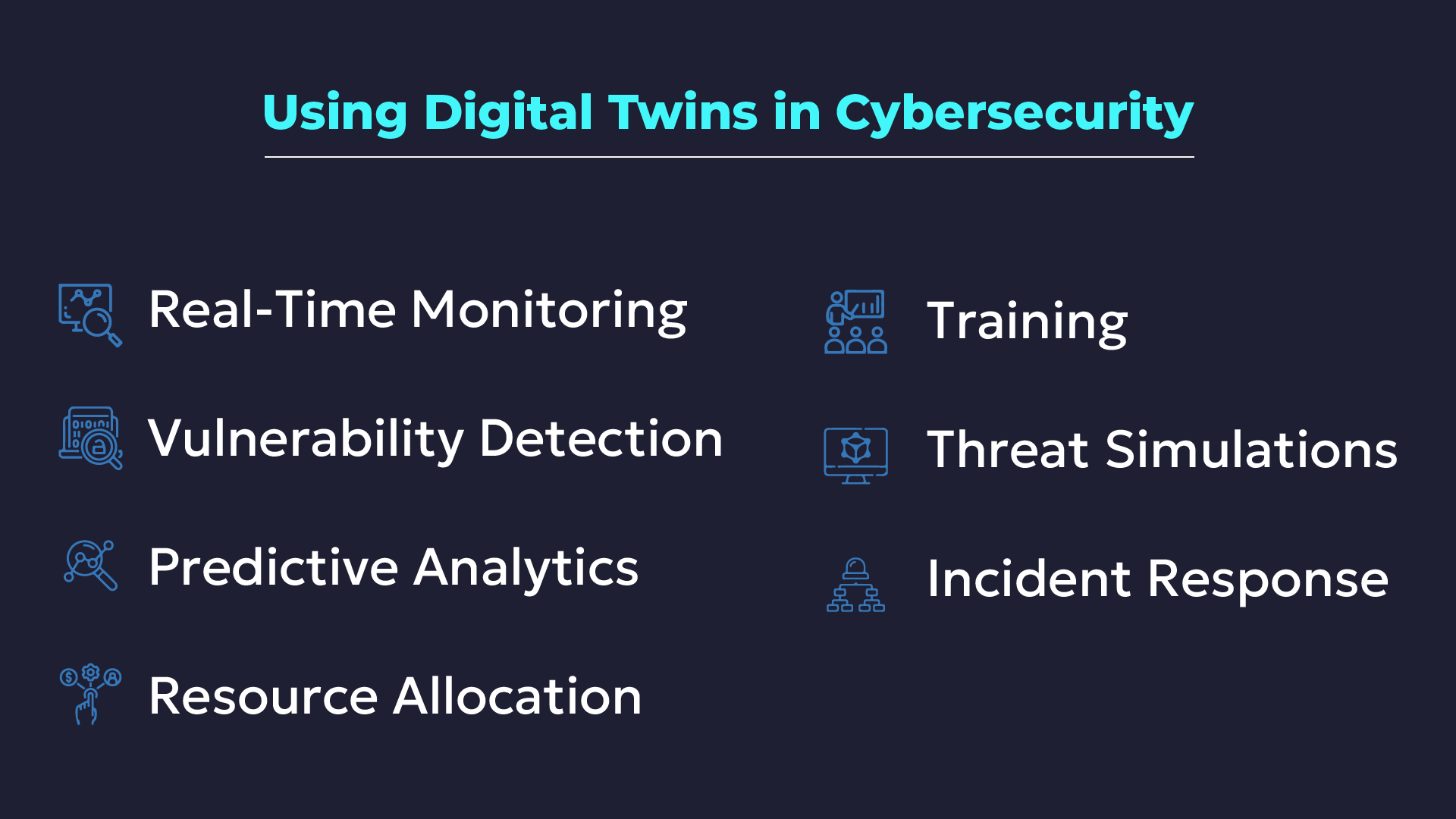
These virtual replicas leverage machine learning for real-time cyber threat detection (as above), while also giving greater access to usage trends for reporting (as for leadership decision-making and compliance). They allow security teams to cover far more complicated and vast systems than previously possible.
But they can also function as sandboxes, forecasting through analytics and running targeted cyber threat simulations. These can not only help test a system’s defenses, but also see how they respond to failures, to help design effective incident response and disaster recovery plans.
Working with digital twins of real systems also enables more realistic training scenarios, and helps design proactive vulnerability detection tests, such as through chaos engineering.
Just as digital twins provide more exposure to attackers, they also give security teams larger (and more realistic) test spaces, which can also be more granular and accurate to the real thing.
What’s Next
The cybersecurity applications of digital twins are still emerging, but as the models themselves become more affordable and scalable, more organizations can make use of these benefits.
As AI continues to improve, we’ll see cybersecurity leveraging this digital transformation tech in bold new ways, attacking virtual versions of systems before they go live, testing access vulnerabilities, and applying known cyberattack strategies to see how they hold up, both before rollout and during live run-time.
As we led with, digital replicas of the real can help us gain more insight into these behaviors by giving cybercriminals fake targets to hit.
GE Global Research is one company using this approach now, with what they call “digital ghosts.” By creating digital twins of complex sensor layers, systems learn to recognize if behavior is wrong as it happens, allowing swift recourse.
As Justin John, executive technology director at GE Global Research tells CSO:
“The reality is I can predict pretty well how things are supposed to operate, especially if I have the controls integrated with my digital twin model… We’re using a twin, but we don’t want the attacker to know about it, so it’s a digital ghost.”
Such an approach can be applied in an operational data center, looking at traffic and its behavior to immediately detect abnormalities.
These digital twins flag that something’s wrong and then also help detect what it is.
“That alone typically takes operators days or weeks to pinpoint where the problem is. The digital ghost does that within seconds.”
Conclusion
As the wise master of Bruce Lee’s character in Enter the Dragon says:
“Remember the enemy has only images and illusions behind which he hides his true motives. Destroy the image, and you will break the enemy.”
So, too, will the digital twin cybersecurity systems of the future help us to unveil cyberattacks—not only as they happen, but even beforehand, drawing the attackers into honey traps that function like the mirrored walls from the film.
By offering proactive threat simulation, and real-time monitoring that understands the correct behavior, digital twins can transform our cybersecurity.
References
TwinPot: Digital Twin-assisted Honeypot for Cyber-Secure Smart Seaports, arXiv:2310.12880
How Digital Twins Could Protect Manufacturers From Cyberattacks, NIST
Avatars: Are we ready for our digital twins?, BBC
Digital twins: When and why to use one, McKinsey Digital





