Cybercrime keeps on surging.
Late last year, US Deputy National Security Advisor for Cyber and Emerging Tech Anne Neuberger said that the annual average cost will reach $23 trillion in 2027, worldwide.
Breaches are constant and costly, and AI is both helping with defense and exponentially proliferating attacks, driving a staggering 1,265% increase in phishing attacks in 2023, per SlashNext.
Supply chain attacks are coming on strong, with Gartner estimating the damage ($46 billion in 2023) will reach $138 billion by 2031.
Workforces are increasingly distributed (with an estimated 71% of companies offering some form of remote work), and depending on who you ask, we are somewhere around 4 million cybersecurity workers short of global need, even with AI implementation rising. An ISC2 survey showed that 90% of organizations have current skills gaps in their security teams.
In our last cybersecurity roundup, we profiled the National Public Data breach, where 2.9 billion records of personal data were stolen, covering a huge chunk of the US, Canada, and UK. Now Wired reports that the firm is run by a single person, and on machinery that costs around $2500 total.
With hundreds of millions of people already impacted by the fallout.
Against this backdrop, we launch our new series—Cybersec Risk Focus—to profile a specific attack type or concept critical in cybersecurity now, and we debut with Zero Trust Architecture (ZTA).
While not a form of risk, ZTA is a critical means of protecting against this litany of attacks, and one that’s surging in popularity and attention.
Instead of trying to guard the walls of your organization to keep bad actors out, ZTA is geared at segmentation, with continued verification, ensuring that when an inevitable breach happens (and per the stats, it probably will), lateral movement is prevented, limiting the potential damage.
Instead of protecting the outside and only letting approved individuals in, ZTA assumes that no one has a right to be inside, unless they can prove it, and continue to do so.
Why Zero Trust Security
This concept is not new, dating back more than 25 years, geared on offering no default trust for anyone inside a system. But for decades it’s often been more conceptual than practical.
Back when more workforces were primarily on-site, this seemed far less necessary. Even with critical data, employees could be checked coming in and out of a building. They’d be seen in person and have to sign into a personal workstation, all a reasonable backdrop for our current, firewall-driven defense system: sign in to enter, and then move freely on need.
Zero Trust, to extend the metaphor to the physical world, is more like checking ID in the parking lot, scanning on entry, a unique keycard at your office, biometric machine sign-in, multi-factor on each application. Separate keys for meeting rooms, printer, kitchen.
In the real world, this looks like overkill.
But today, even if you’ve still got a workforce that’s entirely on-site, it’s doubtful your data and everyone accessing it—including their systems and all their integrated tools—are as well.
This is the challenge ZTA aims to solve: how do you protect a vast, and shifting, field of connections and entities, be it people, devices, and software, that are interconnecting every day and at all hours?
Even if your own security is outstanding, how do you know that none of your third-party associates, or anyone in your vast tree of interconnections, is that one individual with his $2500 setup, bad security, and access to too much data?
We’ve written a lot about ransomware, and consistently a lack of sufficient security on one entry proves to be a gateway for bad actors to attack the entire organization.
Use Cases
The shift to a Zero Trust approach to cybersecurity is well underway, with Cisco reporting that 86% of surveyed organizations had started implementing Zero Trust, though only 2% had reached what they deem to be a full implementation across Zero Trust pillars.
Gartner’s own survey from April finds 63% of organizations underway on a full or partial Zero Trust implementation. And 56% indicated they’re pursuing it because it’s cited as the best approach, even as many remain unsure what the top practices should be.
To help with this question, the National Institute of Standards and Technology (NIST) collaborated with various organizations (including AWS, Cisco, Google Cloud, IBM, Microsoft, VMware, and more) in an effort to use commercially available technology to document 17 ZTA implementations, including use cases, lessons learned, and technical information to use as a guide.
Their use cases for access control in Zero Trust include:
- ID-Access (by the company itself, a trusted/authenticated third party, or by a known/registered third party): for access that’s full or limited, stolen IDs, using bring-your-own-device (BYOD), requesting a resource or internet domain, based on a single business process (to be revoked when done), and for cases that stack (each needing additional authentication checks)
- Guest Access: requests for public access and resources only
- Confidence Level: for subjects with an active session to a resource, when user reauthentication or endpoint reauthentication fails, compliance fails, for violations of data use policies, attempting unauthorized access to an additional resource, requesting access from an endpoint already flagged as suspicious/compromised
- Service-Service Interaction: requests via API calls, with both subject and resource being uniquely identified and authenticated, when both are in enterprise-operated infrastructure, cloud-based, between containers, from enterprise to enterprise for maintenance, reconfig, etc.
- Data Level Security Scenarios: with variations in data sensitivity and subject classification, access granted or restricted by identity, endpoint type, or other attributes such as BYOD, cases where subject has active access session, temporary high-level data access, ensuring download/copy of sensitive data is encrypted or has other additional protection until an additional challenge is passed
Challenges
Implementing and maintaining a segmented, always-vigilant defense isn’t an easy change, of course, with much of the challenge being mental and cultural.
Zero Trust adoption challenges include:
- Organizational Buy-In: Going from “verify then trust” to “never trust” is a significant change in approach, and push-back is inevitable. From concerns about the practicality and necessity of the change to a belief it’s only for the largest or wealthiest of organizations, ZTA success requires clear communication on the goals, implementation process, scale, and benefits. It also needs buy-in.
- Structural Issues: Without visibility on business applications, assets, user roles, usage patterns, transactions, architecture, and current attack surfaces, it can be hard to grasp what ZTA is going to look like for any organization. This kind of clarity and understanding is essential for crafting a Zero Trust deployment strategy.
- Technical Challenges: ZTA doesn’t require wholesale technological change, but the capacity must be there for a standardized policy that can be distributed and enforced. This means identifying potential gaps, determining what approach is best for the company, and developing a clear understanding of what the risk tolerance is going to be at every level. While the goal will be to leverage existing technologies first, it may not be possible in every case.
Implementing Zero Trust Policies
Here are recommended Zero Trust best practices for getting tangible, scalable benefits from the approach:
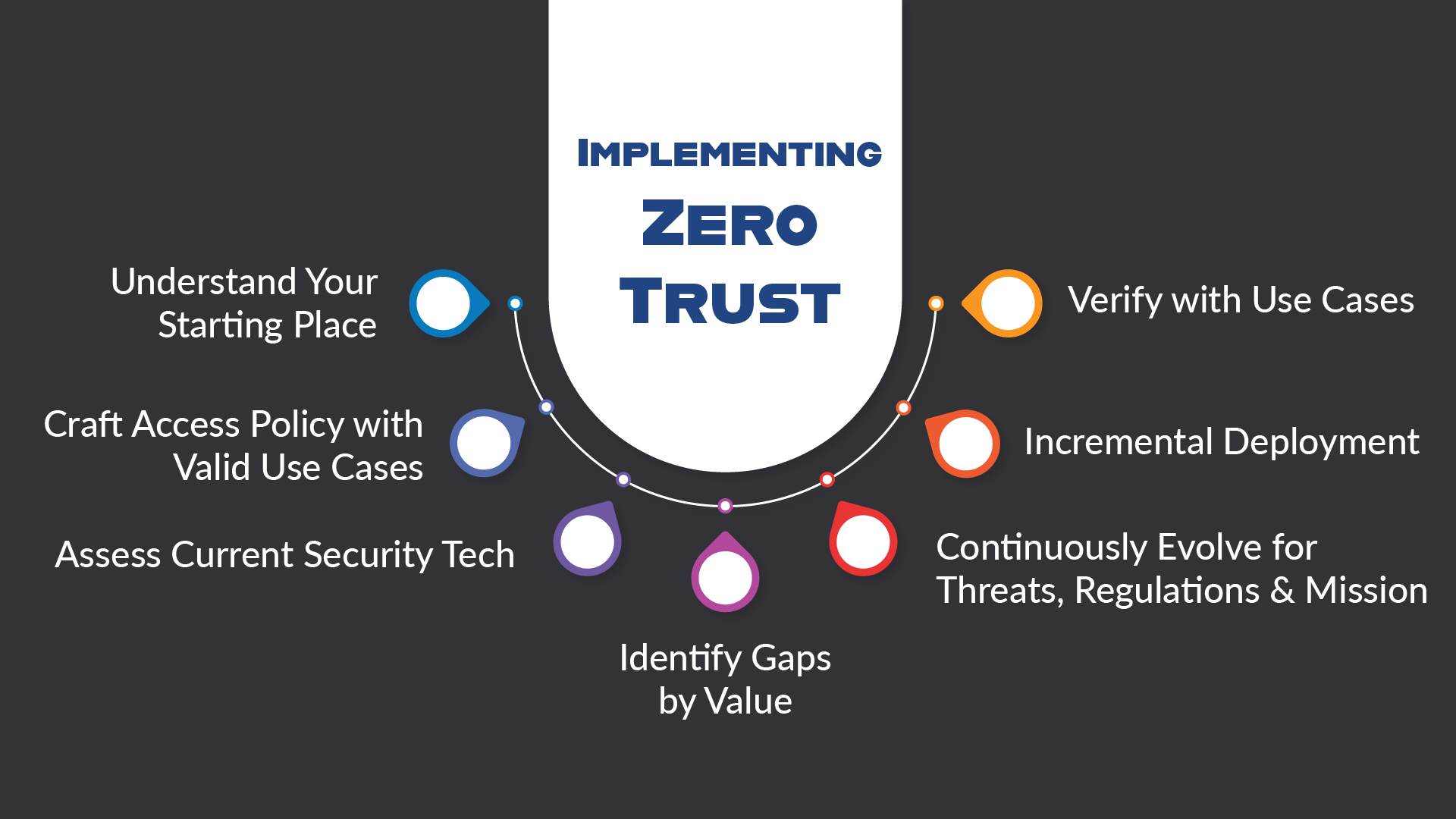
- Understand Your Starting Place: Identify all resources that are active and in use, from hardware to software, including applications, data, and services. Cover everything, using tools to monitor traffic. Knowing what’s needed begins with understanding how access is happening now, and by whom. Ideally once such a survey is completed, it should be repeated at regular intervals, once ZTA policies are in place.
- Craft Access Policy with Valid Use Cases: This is theoretically simple: who is allowed to access what, from where, and when? But in practice, this can spiral quickly. Working out from denying everything by default, use insights gained above to target your approach, such as by securing remote work access first or a focus on preventing lateral movement. The priority of these decisions can then guide policy.
- Assess Current Security Tech: Unless you’re just starting out, there will be existing security tech in use, from network firewalls to access control management systems to intrusion detection. Analyze each in light of the ZTA model to see if it can be leveraged or repurposed. You can also use this knowledge to ensure any additional pieces being brought in integrate seamlessly.
- Identify Gaps by Value: ZTA means breaking away from an “outer wall” concept of defense, and instead segmenting the infrastructure by importance. These divisions help limit the impact of breaches, and also make monitoring easier. Enforce access control at various levels: application, host, and network, by priority.
- Incremental Deployment: Continuous monitoring is a great place to start, giving the capacity to audit implementation as it grows. The ZTA system is geared around making access decisions and then enforcing them, and MFA will be critical in this. The order of roll-out depends on the plan, prioritizing data security, tracking user behavior, and scaling with AI analytics.
- Verify with Use Cases: Zero Trust requires continuous verification, which should be measured against use cases. Sensitive health records might require multiple layers of authentication, for example, but regardless, observing the network flow is essential. If you have selected accurate use cases, they should reflect real-world behavior, making them ideal to test against.
- Continuously Evolve: Cybersecurity best practices in general dictate staying on top of a constantly evolving threat landscape, and that means updating your ZTA policies and implementation as necessary to ensure coverage. Data priorities, scale, and user behavior will also shift, as may regulations restricting access or ensuring compliance. Real ZTA requires constant monitoring, and the better the above steps have been implemented, the more ready the organization will be to add additional use cases and adjust access policy, measure value, incrementally deploy, and test.
Conclusion
With a business landscape that’s increasingly cloud-based, remotely accessed, and interconnected with third-party systems, protecting all your company’s potential vulnerabilities has never been harder.
The appeal of Zero Trust is that it is not a one-breach-opens-to-all defense; when properly implemented, it improves network security and threat detection, mediates third-party security risks, and allows for prioritization. Breaches will happen, but with ZTA, you can more easily locate, lock down, and limit the potential damage when they do. You can also ensure you are putting the most energy to protecting the most precious aspects of your system.
Implementing Zero Trust fully requires a cultural change in how you approach security, which means getting full buy-in, repurposing or upgrading legacy systems, and enacting careful, ongoing oversight and management.
It’s also arguably our best shot at stemming the rising tide of cybercrime.
References
Digital Press Briefing with Anne Neuberger, Deputy National Security Advisor for Cyber and Emerging Technologies, US Department of State
The State of Phishing 2024, SlashNext
Leader’s Guide to Software Supply Chain Security, Gartner Research
Security News This Week: The FBI Made a Crypto Coin Just to Catch Fraudsters, Wired
Security Outcomes for Zero Trust, Cisco





