Passwords have probably been around as long as language. As Robert McMillan notes for Wired, sentries have used them throughout recorded history. Shakespeare starts Hamlet with a call out, which the character Barnardo answers with a passphrase to identify himself.
They’ve been with computing since the start, dating back to MIT’s Compatible Time-Sharing System (CTSS) in the 1960s. And even then, there was a data breach, when the system screwed up and dumped everyone’s passwords out in the welcome message.
(McMillian also profiles how researchers were stealing passwords from the start to get more time on the machine, showing that, as a security system, it’s never been all that effective.)
And yet here we are, still tied to them 60-plus years later.
We’ve written about good password policy before, but even that is only so useful. Everyone’s in the same bind: With most of us having more than 100 password-protected sites we need semi-regular access to, we’re reduced to either re-using something we can remember (very bad idea), keeping paper notes like a sticky-on-the-monitor (also not a great idea), taking advantage of in-browser-saving (bad as well), or relying on a third-party solution provider, like a vault, at a personal cost and extra step of overhead.
Anyone who’s ever had to type a complex password into a smart device’s virtual keyboard for signing in shares the frustration at a woefully insufficient and overburdened solution that is likely not going to persist for another 10 years, let alone 60.
Between the difficulty in wrangling all these complex passwords to an unprecedented surge in cybercrime, one of 2025 cybersecurity trends is a renewed drive for alternative solutions. Most of the major tech players are working hard to move us to a world of post-password authentication.
In today’s edition of The PTP Report, we dive into these alternate authentication technologies. We look at why it’s a problem, what the future may hold, and why any of this matters.
The Growing Problem with Traditional Passwords
Passwords are a low-tech and fairly universal solution. But they’ve been around for centuries, so why’s this suddenly a problem now?
We’ll get to cybercrime trends in a moment, but regardless, technological advances are raising the stakes in various ways.
Have you ever seen algorithmic estimates of how long one of your passwords would take to crack (when you do really well, it may say three million years, etc.)? That probably makes you feel good, because it sure beats your pet’s name and lucky number.
But that estimate is using conventional computing.
Quantum computing advances like Google’s Willow chip are going to shift this paradigm. Their system reportedly computed a benchmark that would take the world’s fastest conventional supercomputers 10 septillion (or 10 to the 25) years (much older than the age of the universe), in just under five minutes.
More pressingly, AI advances in video and audio technology are raising deepfake security threats, making it possible that someone else can look, sound, and potentially even generate unique responses just like you.
And while this doesn’t necessarily invalidate using a secret word for authentication, it does raise the challenges of recognition, especially online.
The combination of AI and phishing attacks also ups the risk, making it harder for any of us to know when we’re dealing with reliable sources.
[For more on the dangers of this combination and the risks improved phishing poses to security, check out this article by PTP’s CEO Nick Shah.]
In other words, it’s never been more important for us to be able to prove we are who we say we are.
The Stakes Keep Going Up
At the same time, attacks on our accounts are increasingly rampant.
Breaches are leaking passwords for all of us (with some 350 million people worldwide impacted in 2023 alone), and frequently these get compiled into Dark Web lists that get bought and sold. Criminals take these lists to power brute force attacks that try username and password combinations all over the web, looking for inevitable password re-uses to exploit over hundreds of sites.
At this point, most everyone knows that password reuse is a bad idea, but according to a Google Security Survey, 65% of people still admit to doing it.
And as covered above, AI tools make this even worse, with increased capacity to crack weak passwords in seconds or craft far more convincing phishing scams that catch up even security professionals.
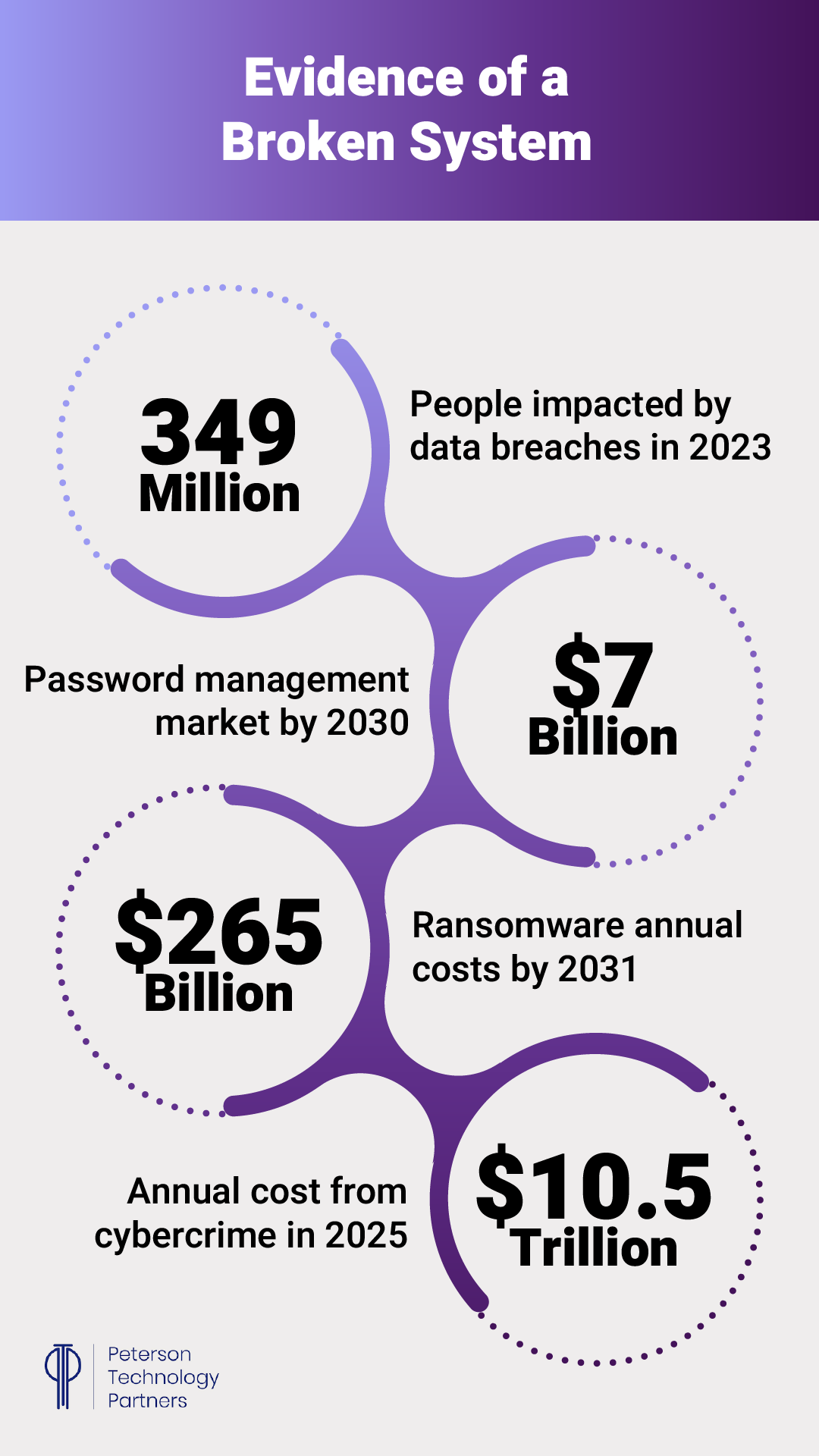
The frequency of these attacks is skyrocketing, with phishing attacks (often targeting passwords) succeeding at some 71% of organizations, per the Proofpoint 2024 State of the Phish report.
Password Alternatives
As mentioned, a number of the biggest tech companies are at work attempting to move past passwords, so let’s look at some of the most promising (and controversial) options being put into play.
Biometric Authentication
The most obvious way to prove who you are is by using your own physiology. We have various unique, distinguishing characteristics, including fingerprints, voice, signature, iris/retina, palm veins, and, of course, DNA.
“Biometrics” in general refers to these distinct, measurable characteristics, and Apple’s system may be the most famous, with their TouchID for fingerprints first coming into use back in 2013, and their FaceID facial recognition coming online in 2017.
Despite numerous attempts to fool or hack these technologies over the past decade, they have remained consistent and helped overcome some traditional customer resistance to giving biometric data for access.
And by storing the data on-device, Apple has avoided some privacy concerns around the movement and centralization of biometric data as in a database which could easily be used for alternate ends.
Meta has long attempted to use the technology without this safeguard and has run into significant challenges. In the 2010s, Facebook built one of the largest facial recognition systems in the world, capable of automatically matching faces in images to “tag.” Privacy concerns from the practice reached a head in 2021, resulting in their promised end to the process and deletion of their database of some one billion faces.
This has accompanied legal issues, like a $1.4 billion settlement last July, per The Washington Post, of a case in Texas, and drawn scrutiny from regulators around the world.
Meta is now returning to the practice in testing, allowing locked-out users to use biometric facial recognition to get back in. Should this be successful, it’s reasonable to expect an increase in the application of this approach.
OpenAI’s Sam Altman has also long been interested, believing the increase of AI sophistication also requires a need to be able to verify one’s humanity, remotely, in a way passwords alone never can.
His Worldcoin (now World Network) project makes use of a physical Orb to scan a user’s iris and create a unique digital identifier. The idea is that the Worldcoin Orbs could be distributed to physical stores or coffee shops, enabling users to generate their own identifier there, or even via the mail, where, once used, the physical Orb could then be sent on.
But data privacy concerns, as with Meta, have hampered this process, with regulatory challenges launched in both Europe and Asia.
And aside from the obvious privacy concerns in allowing companies to authenticate you with biometric data, there are also greater dangers in the potential for hacks and breaches.
While you can always change a stolen password, you can’t change your biometrics.
The One-Time-Password (OTP)
A far simpler means of moving away from user-kept passwords is through One-Time-Password (OTP) systems. These operate exactly as the name suggests: with a desired vendor giving you a single-use password through an already-authenticated channel, such as personal email or cell phone.
We all use these for password resets, and they come in various forms, from system-generated single-use passwords to authenticator apps to so-called “magic links.”
Magic link authentication works by generating a unique, single-use URL which the user can access without even needing a password, temporary or otherwise.
These have the benefit of being simple for end-users, but they’re far more complex for the issuers, requiring a cryptographically secure token that must be properly generated and handled to function correctly.
These tokens are the key to authenticating a user through a provided link, whether it’s delivered via email or SMS.
And while OTP solutions are easy for end-users and work well as a form of multi-factor authentication (MFA), or as a backup/secondary means of verifying a user, they can be particularly risky with the AI-driven spike in phishing, where clicking on links provided by third parties is increasingly ill-advised.
They can also be prone to interception, enabling cybercriminals to potentially swap them out for compromised variants.
Passkeys
Passkeys are an attempt to deliver the best of these various solutions. Using codes generated by public key cryptography, they don’t need to be memorized or written down, because they are stored on your device or in a trusted digital location. Access to these is already protected by alternate means, such as biometrics or trusted PINs.
Passkeys require two separate parts (a public key and private key) to work, and these cannot be reverse engineered from either side, meaning a cybercriminal would need both the device that stores the key and your means of signing in to even attempt to gain access.
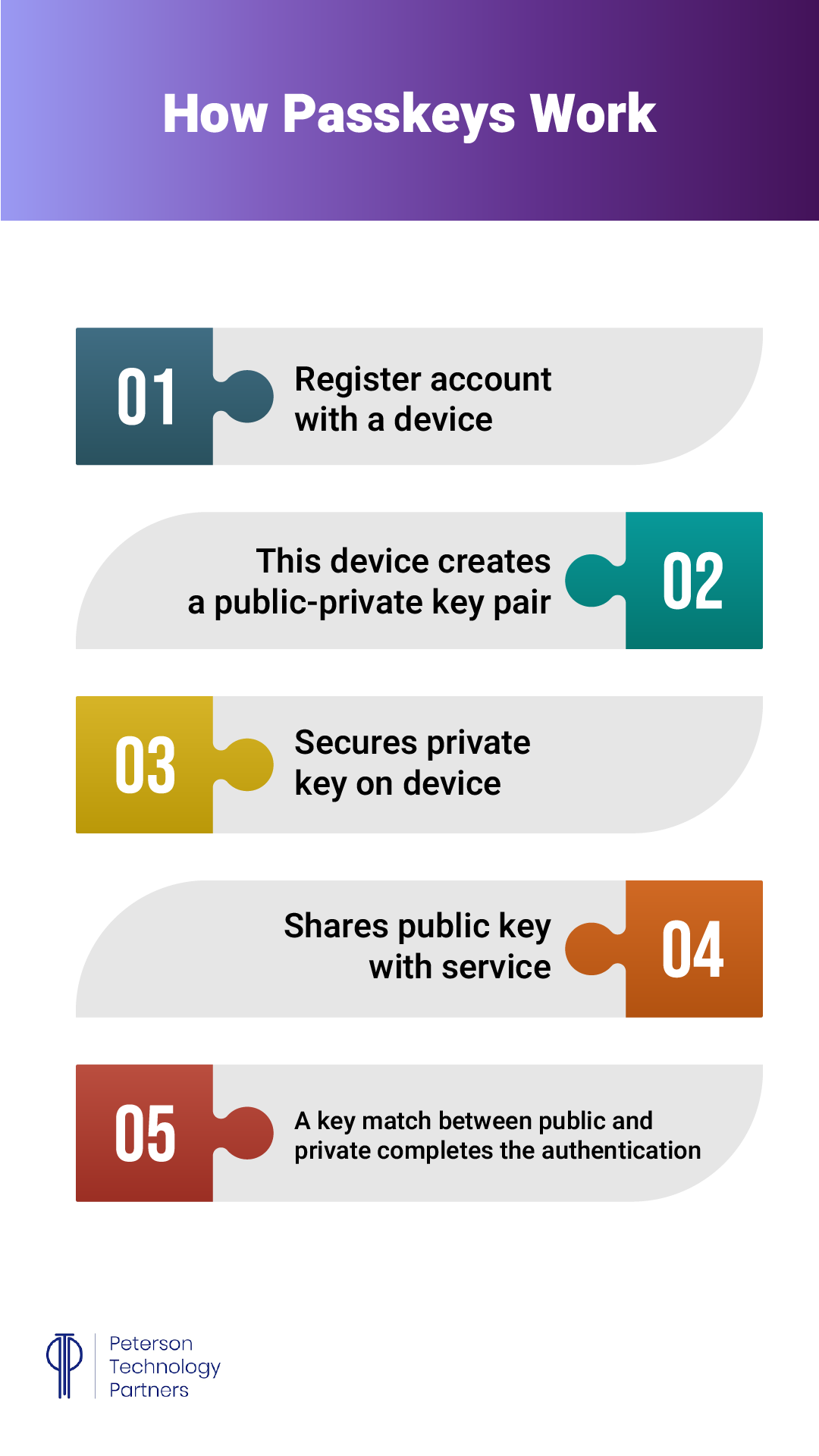
Google, Apple, Microsoft, and Amazon have all started supporting passkeys, and the Fast IDentity Online (FIDO) Alliance exists to generate and maintain standards across vendors. Check out the alliance’s site for more information on the standards, their goals and members, and more details on how the system is designed to work.
Passkeys are now in use at hundreds of sites, supported on most major operating systems, and through the most popular browsers, and when they work well, they seem like a magic bullet for password-weary end users.
But passkey adoption is not without its own challenges.
As you move across systems, one problem arises in the unique way it’s implemented. As different companies must come together for the solution, users often receive unique pop-ups that can be unexpected and even confusing. Passkey systems push users back into a vendor’s own ecosystem, which can also complicate the workflow.
And while they’re highly resistant to phishing (you can’t accidentally give it away), they don’t work in all exchanges, sometimes forcing users to fall back on alternate access methods, like passwords.
By being tied to a specific device, it may fail when you need to access an account online using hardware from another company (from iPhone to Windows machine, for example).
Many password managers can now work with passkeys, aiding with some of the cross-platform difficulties, but this one again can require using a paid service and additional step as with traditional passwords.
How PTP Can Help
As we see a rise in AI-powered security solutions, it can be easy to overlook the power of the simpler solutions, like implementing MFA, quality security training, and monitoring user access.
With this move away from passwords and toward solutions like passkeys becoming increasingly important for both security and customer satisfaction, consider us to fill your needed security and development positions.
From training to ongoing support for your unique needs to account recovery to alternate forms of authentication, PTP can help you find the best professionals, whether you need them onsite or off.
Conclusion
The emergence of new AI tools, privacy, and biometrics are all considerations that go hand-in-hand. Because as useful as it may be to tie yourself directly to a digital account, this also distributes your likeness, specifically identifies you as a person (rather than an account name) to online behavior, and exposes unalterable aspects of yourself to potential exploitation by cybercriminals.
Many nations already regulate biometrics (though at radically differing levels), but as more companies employ these solutions to save us from a broken password system, there will undoubtedly be increased scrutiny.
AI pioneers and security experts alike are agreed on the need for better authentication, and security approaches like zero-trust require more regular proof of a right to access, making the death of the password as our primary means of access inevitable.
Whether it’s passkeys, more extensive biometrics, or yet-to-be-discovered solutions that win mass adoption, the effort is no longer just about protecting accounts or for verifying you are who you say you are.
It’s also about proving that you’re a human being.
References
The World’s First Computer Password? It Was Useless Too, Wired
Meet Willow, our state-of-the-art quantum chip, Google: The Keyword
Meta’s new fix for locked-out users: Scanning their faces, The Washington Post
Sam Altman’s Eye-Scanning Orb Has a New Look—and Will Come Right to Your Door, Wired
Passkey technology is elegant, but it’s most definitely not usable security, Ars Technica





