We begin our bi-monthly roundup of cybersecurity news at the year’s first quarter point with these surprising results from Cloudflare research released in mid-March:
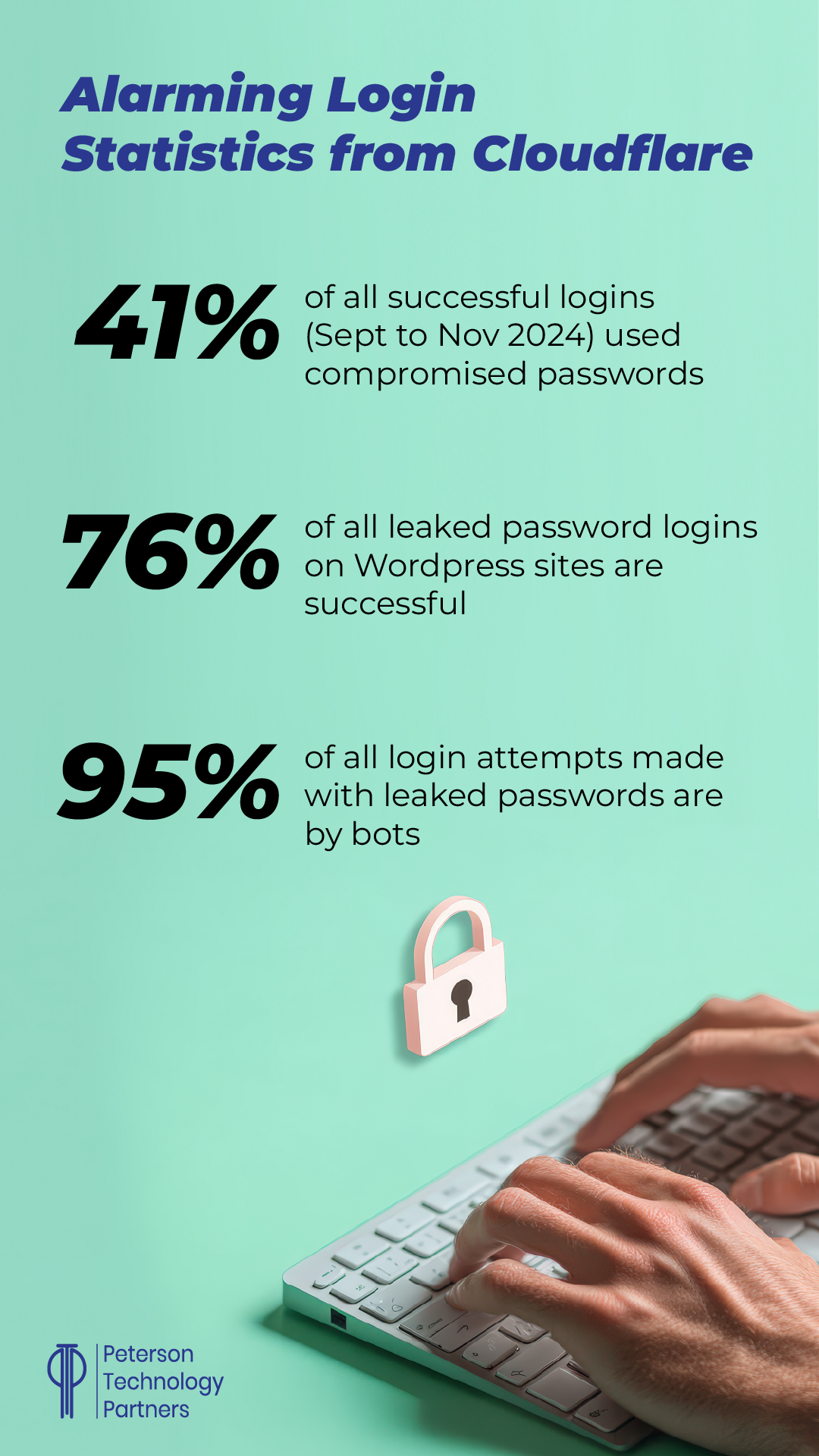
Based on an analysis from late last year on sites they protect, Cloudflare discovered a surprisingly large number of successful logins (41%) used passwords that were already leaked. These included some in either their own database (15 billion records) or available from the Have I Been Pwned website (which we first profiled here).
This included logins for email, streaming services, social networks, and more.
Among platforms, WordPress, with its popularity for content management (used by some 62% of all websites for content management where the provider is known, per W3Techs), had some of the most striking password security issues.
76% of all logins using leaked password for WordPress sites were successful (with 46% of them coming from bots).
With credential stuffing being a common first step of cybercrime attacks that target businesses, this is a disturbing indication of just how many of our virtual doorways are standing unlocked.
In today’s report, we overview findings and business news, move to government updates and cyberwarfare, and consider a bevy of novel or newly popular attack types, across targets.
Parsing the Period’s Cybercrime News and Business Updates
It’s nice (if rare) to be able to include good news in one of our roundups: Ransomware payments actually went down in 2024.
Per Chainanalysis’s annual crime report from February, the $814 million known to be paid out represented a 35% drop from the $1.25 billion of the prior year. From July to the year’s end, it was just $321 million.
Ironically, this doesn’t reflect the volume of ransomware attacks overall, which were up from 4,400 in 2023 to 4,463 in 2024, as tracked by security firm Recorded Future and reported by Wired.
Paid-out ransom amounts have gone down and back up before, as from the $1.07 billion in 2021 to $655 million in 2022, but nevertheless, successful law-enforcement actions, increased publicity, popular ransom failures, and improved cybersecurity defenses may be yielding some dividends, at least in terms of stopping ransom payments.
While on the subject of defenses, big cybersecurity acquisitions are back in the news, with Microsoft’s acquisition of cloud data security firm Veeam and Google once again lining up a deal to acquire Wiz (for $32 billion this time).
The Microsoft Veeam deal brings a service focused on quick recovery from data loss, ransomware attacks, and other cybersecurity incidents for aid in AI applications, but pales in comparison to the scale and potential significance of the Google Wiz acquisition.
If it goes ahead, it would be the largest in Google’s history, and adds top-level, pre-emptive cloud security to their current offerings.
Two years ago, Google acquired Mandiant for $5.6 billion to be the core of their intelligence and Security Operations Center offerings.
With Wiz, which was founded by ex-Microsoft engineers and has a strong reputation for security in Azure deployments as well as the other major providers, they gain greater protection for potential attack points and aid to developers before deployment.
The deal could be a big cybersecurity win for Google and a blow to Microsoft, though it could run afoul of regulators who are already eying Google for potential breakup.
Government Cybersecurity Trends in 2025
Speaking of regulatory scrutiny, the FTC is also continuing an antitrust probe of Microsoft started under the Biden administration, according to Bloomberg, looking at their behavior in a number of fields, including cybersecurity and AI.
At the state level, New York has sued Allstate over a pair of data breaches, suggesting that not only did they fail to notify affected parties in a timely fashion but also that their defenses were far too lax, lacking reasonable safeguard to protect their customers.
New York Attorney General Letitia James told reporters of Allstate’s National General unit:
“National General’s weak cybersecurity emboldened hackers to steal New Yorkers’ personal data, not once but twice… It is crucial that companies take cybersecurity seriously to protect consumers from fraud and identity theft.”
Cybersecurity and the DOGE Cuts
The federal government’s Department of Government Efficiency (DOGE) has been in the news constantly throughout this period, and some of the reports have concerned cybersecurity, specifically:
- In March, more than 70 employees were terminated from the National Institute of Standards and Technology (NIST), which establishes benchmarks and evaluates safety. This is a large reduction from the 500 that were rumored to be released in February.
- Outlets including Time, CSO, and KrebsonSecurity expressed concern over the nature of requests by DOGE to transfer private employee data via a publicly promoted email address, utilizing password-protected attachments. Such documents are also challenging for virus scanners, increasing the likelihood of malware attacks.
- The actual number and nature of layoffs at the Cybersecurity & Infrastructure Security Agency (CISA) has been a subject of debate, with some 130 being listed in initial estimates. And while some reports have indicated Red Teamers were or were not part, others may be protected by the federal government’s CIO, Greg Barbaccia, who suggested in early March that cybersecurity professionals be exempted from layoffs, as their work is related to national security.
Actions in Response to Chinese Hacks
Following 2024’s shocking reports of mass infiltration of US telecom:
- In early March, the US Department of Justice announced a Chinese hackers indictment targeting 10 contract hackers and a pair of government officials for decades-long actions against the US, including the Salt Typhoon attacks that made news last year and the hack of the US Treasury.
- A US congressional committee has urged Americans to quit using Chinese-made wireless routers, such TP-Link, citing security threats.
- In reporting by Wired, the Chinese hacker group Salt Typhoon continues to infiltrate telecommunications networks also exploiting vulnerabilities in Cisco routers, a continuation of the long-running hack exposed late last year.
Additional Government Updates
- FBI and CISA cybersecurity updates warned in March that Medusa ransomware-as-a-service attacks, which have impacted some 300 organizations in critical infrastructure dating back to June 2021 (and far more overall) are continuing to escalate. Symantec tracked a 42% increase in these from 2023 to 2024.
- Multiple countries (including UK, France, Sweden) are proposing measures that target encryption, with demands for backdoors and client-side scanning, raising privacy and security concerns. This runs in contrast to the US government’s pivot to increased support for private use of encryption, in light of the Salt Typhoon attacks.
Concerns over Q-Day, or the ability of quantum computers to break widely used encryption technology, have continued to escalate.
Hackers worldwide are believed to have long been gathering encrypted data in a harvest-now-decrypt-later approach, though such a development would also put authentication at risk.
NIST’s post-quantum cryptography is already in place in iMessage and Signal, and probably also to protect critical national security data.
But still at risk are systems running on hold hardware worldwide, from the UK Health Service to energy grids to military hardware to satellites.
Novel Cybersecurity Threats: New or Back Again
We covered the largest cryptocurrency heist in history here. Other attacks of note from February and March of this year include:
- The social network X suffered massive DDoS attacks that led to outages. Debates about the source lingered, though a pro-Palestinian group (the Dark Storm Team) claimed responsibility. Cloudflare protects some of X’s infrastructure, but not all, and those servers that weren’t covered were targeted directly.
- Russian hacker groups are again employing phishing techniques involving fake QR codes to compromise Signal accounts. In response, Signal implemented updates requiring authentication and random interval confirmations. But QR codes are again showing up as a common means of attack.
- Over 2 million IP addresses have been identified targeting edge network devices, such as routers and IoT hardware, to exploit vulnerabilities and take control for a large-scale botnet.
Android-Specific Attacks
- Researchers have identified 331 malicious Android applications, downloaded over 60 million times from the Google Play store. These display compromised ads and attempt to deceive users into revealing personal information.
- Scammers are also exploiting Google Calendar by inserting malicious links into event descriptions and emails, directing users to phishing sites aimed at stealing personal information. As with all links, verify calendar invites before clicking them.
- From reporting by Wired, at least 1 million Android devices, including TV streaming boxes and car infotainment systems, have been found to contain backdoors, allowing scammers to exploit them for ad fraud and other cybercriminal activities.
Data Breaches Across Industries
- The collectibles marketplace Collectibles.com suffered a data breach, leaking sensitive details of nearly 900,000 customers, potentially including full names, email addresses, and transaction records. The cause appears to have been a database lacking sufficient protections.
- The Pennsylvania State Education Association notified affected parties of data breach from 2024 leaking sensitive personal and financial data for some 500,000 members, potentially including Social Security numbers and payment card information.
- A cyberattack at media company Lee Enterprises affected various regional newspapers, such as The St Louis Post-Dispatch and The Buffalo News according to The New York Times. It hampered printing, caused website and subscription issues, forced papers to publish reduced editions, and even disrupted phone systems.
AI Cybersecurity Threats Corner
- A recent Gartner report warns that, by leveraging AI agents, the time required for account takeovers (see below) could be reduced by as much as 50% by 2027.
- Europol has also issued a warning about the escalating use of AI by organized crime groups. Being used for multilingual phishing messages, realistic impersonations, and automated brute force attack processes, it’s bringing a long-anticipated up-scaling to attacks.
- In reporting by Security Week, a third-party, open-source tool called “ChatGPT” but not made by OpenAI has been deployed to target US government organizations and financial and healthcare organizations worldwide. It includes a flaw allowing attackers to inject malicious URLs and force the application to make requests. Firm Veriti observed 10,000 attack attempts from a single IP within just one week.
- ArsTechnica also reported on a hack by researchers that can corrupt the long-term memory of AI systems, such as Google’s Gemini. This indirect prompt injection tricks the model to override defenses and plant long-term memories.
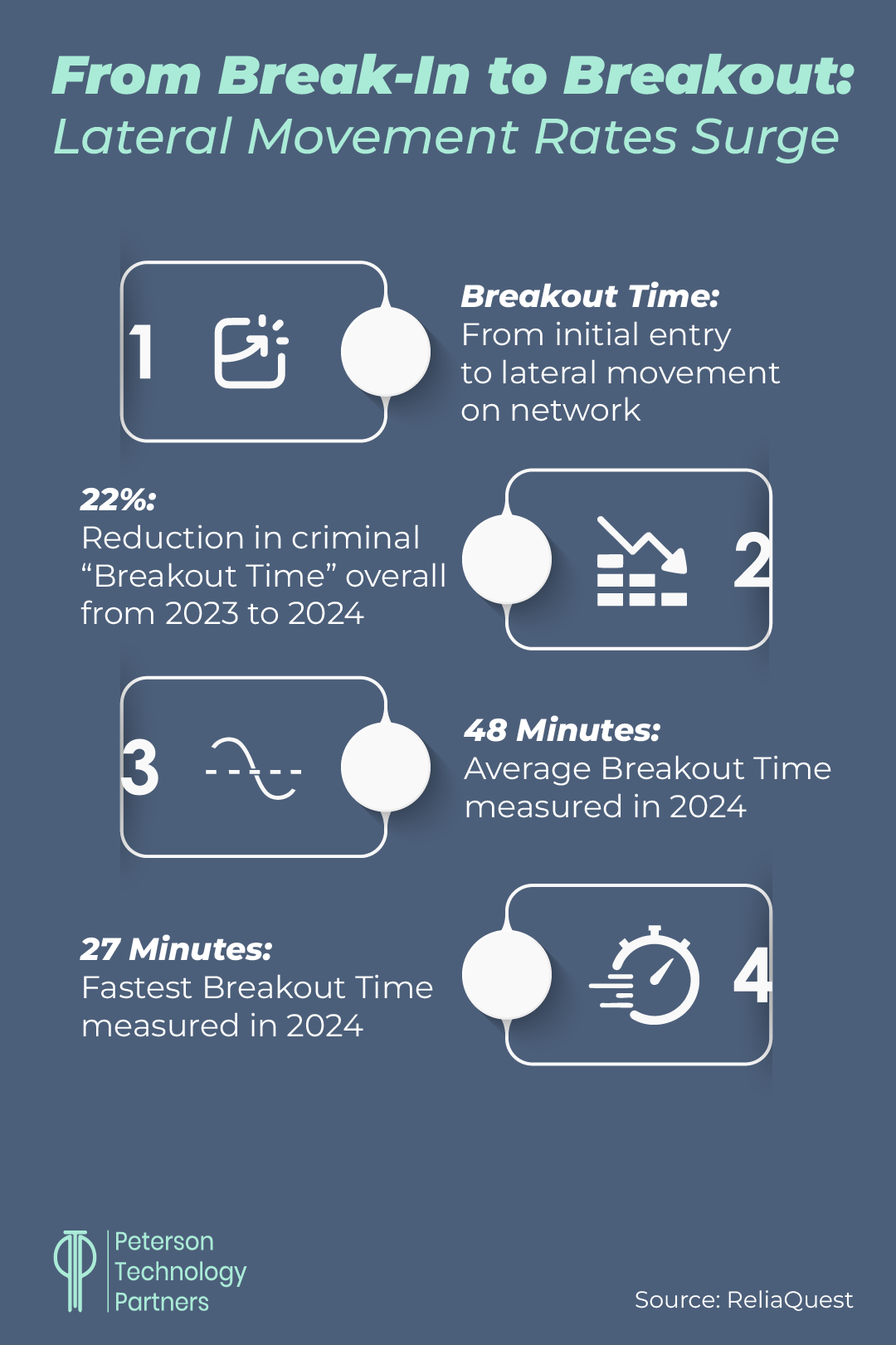
Movement Rates Are Increasing in Latest Cyber Attacks
We opened today with a look at how many compromised passwords are still in use. Now we look at why it matters, as unauthorized access is the first step of multi-tiered attacks, whether they’re aiming to move laterally and exfiltrate data or takeover accounts.
The speed at which this happens, and at which companies respond, is critical to preventing worst-case scenarios. Security firm ReliaQuest has been tracking these rates for years and found the time from intrusion to movement on the network is increasing fast:
Contact PTP for Help Staying Safe: Both Before and After Intrusions
Cybersecurity is a blanket area covering many needs, from protecting your organization from intrusions to responding to incidents when they happen.
Whatever your specific needs, consider PTP. With 27+ years in the business of finding the best talent worldwide, we count cybersecurity among our core specialties, whether your needs are onsite or off—onshore, nearshore, or offshore.
It’s our passion to help organizations protect themselves from attacks and put into place affordable solutions for them to identify and resolve episodes with the least possible harm.
If you’re in need of assistance, consider us.
Conclusion
We write this every month, but it’s unfortunate that there are always too many things cover, due to the sheer volume of incidents, across so many areas. We also try to touch on new areas where possible, so if you’ve missed out on any of the recent news, be sure to catch up on our most recent roundups here:
This concludes this edition of our cybersecurity roundup. Stay vigilant and stay safe!
References
Password reuse is rampant: nearly half of observed user logins are compromised, The Cloudflare Blog
Despite Catastrophic Hacks, Ransomware Payments Dropped Dramatically Last Year, Wired
What’s Behind Google’s $32 Billion Wiz Acquisition? and ChatGPT Tool Vulnerability Exploited Against US Government Organizations, Security Week
Microsoft invests in cloud data firm Veeam Software to build AI products and New York sues Allstate over data breach, alleged security lapses, Reuters
Trump’s FTC Moves Ahead With Broad Microsoft Antitrust Probe, Bloomberg
DOGE to Fired CISA Staff: Email Us Your Personal Data, KrebsonSecurity
CISA denies mass DOGE-led firings, says employment status unaffected, Cybernews
White House exempts cyber pros from mass layoffs; Judge reinstates CISA firings, CSO
Fired VA.gov Cybersecurity Chief Warns Veterans’ Health and Financial Data Is at Risk, Time
Medusa Ransomware Activity Continues to Increase, Symantec Threat Hunter
The Quantum Apocalypse Is Coming. Be Very Afraid and 1 Million Third-Party Android Devices Have a Secret Backdoor for Scammers, Wired
Cyberattack Disrupts Publication of Lee Newspapers Across the U.S., The New York Times
New hack uses prompt injection to corrupt Gemini’s long-term memory, ArsTechnica





